Keeping distributed systems secure
Carnegie Mellon researchers are working to design networks that keep our ever-increasing numbers of connected devices safe and secure.
With more and more devices able to connect to the internet or to one another, it’s becoming increasingly important to ensure that those connections are secure.
When a group of devices—be it computers, sensors, or otherwise—connects and communicates directly with one another, it’s known as a “distributed system.”
Imagine, for example, a group of sensors monitoring the doorways in a particular building. They could communicate with each other to tell you which doors are open and when, which could be used to better secure the building as a whole.
This is an example of a “wireless sensor network,” a particular kind of distributed system. Another would be a group of devices connected to the Internet of Things (IoT) in your home.
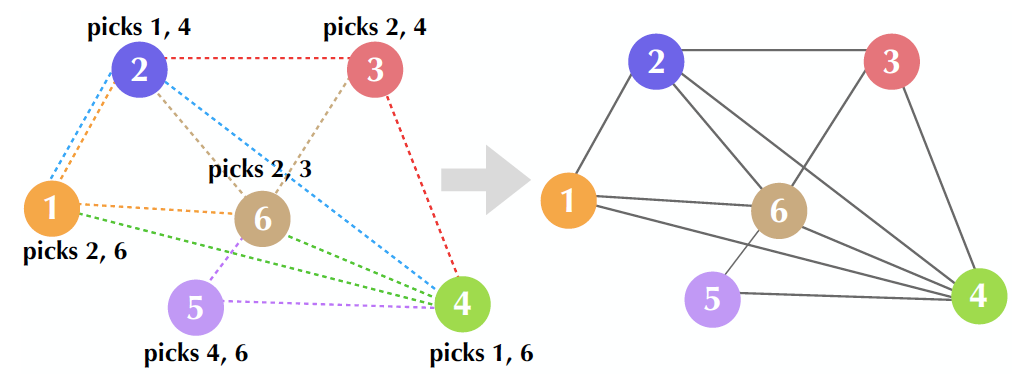
Source: Mansi Sood and Osman Yağan
The nodes pick their connections at random, setting up a graph. This is one way that distributed systems can be established.
With these direct lines of communication, however, there is an increased danger of one sensor or device becoming compromised and taking down the entire system.
Two members of Carnegie Mellon’s Electrical and Computer Engineering Department are working to improve the ways those systems communicate with one another and keep them safe: Ph.D. student Mansi Sood and Professor Osman Yağan.
Sood explained that the work is, “part of our group’s ongoing research on designing secure, connected, and resilient ad-hoc networks for diverse applications including wireless sensor networks and distributed private averaging.”
This paper is part of our group’s ongoing research on designing secure, connected, and resilient ad-hoc networks for diverse applications including wireless sensor networks and distributed private averaging.
Mansi Sood, Ph.D. student, Electrical and Computer Engineering
She accomplished this using a mathematical model known as a “random K-out graph.” Each node of that graph represents a device setting up connections with other nodes in a random, “undirected” pattern.
But why do we need mathematical models like the random K-out graph to represent these networks? “In many distributed systems, connectivity is a fundamental driver of system performance,” Sood says. But, establishing the links between nodes can be costly, and as you set up more, you approach a trade-off between connectivity and cost.
As a result, research like Sood’s is incredibly important to understand how these networks can be designed such that they are provably guaranteed to hold up during an attack. With applications including the IoT and aggregating user data for distributed learning, that privacy and security becomes paramount.
The interdisciplinary aspect of this research also gives Sood the chance to use tools from probability, graph theory, statistical mechanics, and data science all together. She also enjoys doing work with real-world applications and is ready to explore more ways to do this in the future.
“We wish to further explore and design distributed network topologies that are scalable, reliably connected, and resilient and establish analytical guarantees for their performance,” she says.
As more and more of our daily lives move online, we can thank researchers like her for keeping those systems safe and secure.
Sood and Yağan recently won the Best Paper Award at the Institute of Electrical and Electronics Engineers International Conference on Communications in June of 2021. This conference occurs yearly and seeks to drive innovation in the field of telecommunications. Their paper won in the “Communication Theory Symposium” category due to its focus on foundational research into the topic.
